Months ago, I wrote an article (How non-secure ISPs Aid Attackers in Evading Detection) discussing how some malicious actors use certain Internet Service Providers (ISPs) that I categorized as risky. These ISPs fail to thoroughly investigate their customers’ activities and have weak or insufficient controls over their internet services and security measures.
Nowadays, blocking activities by country is becoming less effective due to the widespread use of VPNs and the ease of accessing global hosting services. However, Autonomous System Numbers (ASN) used for malicious activities can be impacted due to it reputation by threats detected using their service. This should be a new approach to monitor new source of potential attacks being able to monitor their associated CIDR.
Building on that article and its conclusions, I’ve come across several interesting cases that confirm certain ASNs associated with ISPs have repeatedly been reported in various online sources for involvement in malicious activities.
This post will cover the process of searching for, identifying, and responding to various ASNs identified as risky. It will also include recommendations and the corresponding KQL queries using different Defender tables:

Identifying Bad Reputation ASN
First, we can gather statistics related to hackers activities over our tenants, such as the number of emails sent tagged as threats, failed sign-in attempts, unsuccessful connection attempts, and other indicators that may signify anomalies or unexpected behaviours. Below, I’ve provided KQL queries to help identify the risky ASNs mentioned at the beggining.
You can adjust the filtering criteria by modifying the line: “| where SuspiciousPercentage > 95 and Total_different_IPs > 10” based on your specific requirements. Here are some examples you can use to gather your statistics:
Emails received detected as a Threat
//Sergio Albea
let CIDRASN = (externaldata (CIDR:string, CIDRASN:int, CIDRASNName:string)
['https://firewalliplists.gypthecat.com/lists/kusto/kusto-cidr-asn.csv.zip']
with (ignoreFirstRecord=true));
EmailEvents
| evaluate ipv4_lookup(CIDRASN, SenderIPv4, CIDR, return_unmatched=true)
| extend GeoIPData = tostring(geo_info_from_ip_address(SenderIPv4).country)
| summarize Different_IPs=make_set(SenderIPv4), Countries= make_set(GeoIPData), make_set(CIDR), make_set(SenderFromDomain), Total_different_IPs=dcount(SenderIPv4) ,Total_emails = count(),make_set(ThreatTypes),Delivered_on_Inbox= countif(DeliveryLocation has "Inbox/folder"), Email_Threat= count(isnotempty(ThreatTypes)),
Email_Valid = count( isempty(ThreatTypes)) by GeoIPData, CIDR, CIDRASNName
| extend SuspiciousRatio = Email_Threat * 1.0 / Total_emails, ValidRatio = Email_Valid * 1.0 / Total_emails
| extend SuspiciousPercentage = SuspiciousRatio * 100, ValidPercentage = ValidRatio * 100
| where SuspiciousPercentage > 95 and Total_different_IPs > 10
| order by Email_Threat
| project CIDRASNName,set_SenderFromDomain, set_CIDR, Different_IPs, Countries,Total_different_IPs, set_ThreatTypes,Total_emails, Delivered_on_Inbox, Email_Threat, Email_Valid, SuspiciousPercentage, ValidPercentageCollecting Suspicious Sign-in attempts
//Sergio Albea
IdentityLogonEvents
| where Timestamp > ago(30d)
| summarize Different_IPs=make_set(IPAddress), Total_different_IPs=dcount(IPAddress) ,Total_sign_attempts = count(), Suspicious_Sign_attempt = countif((ActionType has "OldPassword") or (FailureReason has "WrongPassword") or ( FailureReason has "validating credentials due to invalid username or password.") or ( FailureReason has "The account is locked, you've tried to sign in too many times with an incorrect user ID or password.") or (FailureReason has "Authentication failed.") or (FailureReason has "UnknownUser") or ( FailureReason has "The user account is disabled." )),
Success_Sign_attempt = count( ActionType has "LogonSuccess"),
Issues_Sign_attempt = countif((FailureReason has "The session is not valid due to password expiration or recent password change.") or ( FailureReason has "General failure")) by ISP, Location
| extend SuspiciousRatio = Suspicious_Sign_attempt * 1.0 / Total_sign_attempts, ValidRatio = Success_Sign_attempt * 1.0 / Total_sign_attempts, IssuesRatio = Issues_Sign_attempt * 1.0 / Total_sign_attempts
| extend SuspiciousPercentage = SuspiciousRatio * 100, ValidPercentage = ValidRatio * 100, IssuesPercentatge = IssuesRatio * 100
| where SuspiciousPercentage > 90 and Total_different_IPs > 10
| order by SuspiciousPercentage
Once we have this information collected, we can verify the reputation of the ASN on different places such as urlhaus.abuse.ch/asn/ASNNumber/. I will show you some examples about identified ASN with high percentage of suspicious activities:
ASName: PONYNET / ASNumber: 53667
The hosting provider PONYNET is owned by a company called FranTech Solutions, which is often referred as “bulletproof host“. This term can be recognized by malicious actors as a services that tolerates or turn a blind eye to malicious activities like malware hosting, phishing, spamming, or botnet operations. This reputation attracts cybercriminals, making PONYNET a frequent target for abuse reports.
This ASN appeared multiple times in various logs, delivering email threats and initiating suspicious network activities. As a result, I reviewed its reputation:
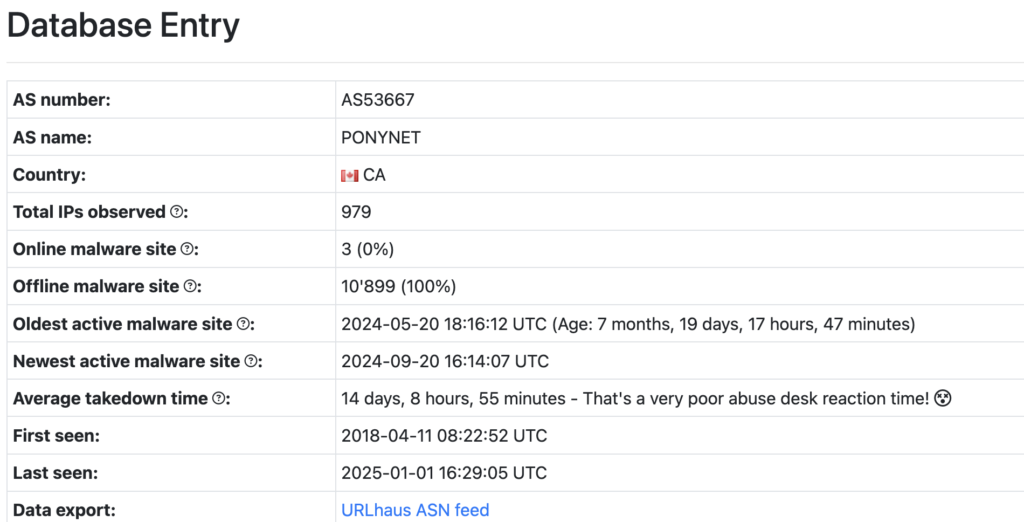
You can use the following KQL Query to identify Device Network Events from specific ASN (as PONYNET in this example) and also check the reputation of their IPS into AbuseIPDB:
let CIDRASN = (externaldata (CIDR:string, CIDRASN:int, CIDRASNName:string)
['https://firewalliplists.gypthecat.com/lists/kusto/kusto-cidr-asn.csv.zip']
with (ignoreFirstRecord=true));
DeviceNetworkEvents
| evaluate ipv4_lookup(CIDRASN, RemoteIP, CIDR, return_unmatched=true)
| where CIDRASN == "53667"
| extend AbuseIPURL = strcat("https://www.abuseipdb.com/check/", RemoteIP)
| extend GeoIPData = tostring(geo_info_from_ip_address(RemoteIP).country)
| distinct DeviceName, RemoteIP, ActionType,RemotePort,AbuseIPURL, AdditionalFields,CIDRASNName, GeoIPData, InitiatingProcessFileName, InitiatingProcessCommandLine, InitiatingProcessAccountNameASName: Drei-K-Tech-GmbH / ASNumber: 200373
Another case is Drei-K-Tech-GmbH which is directly identified as under control of cyber-criminals by URLHaus:
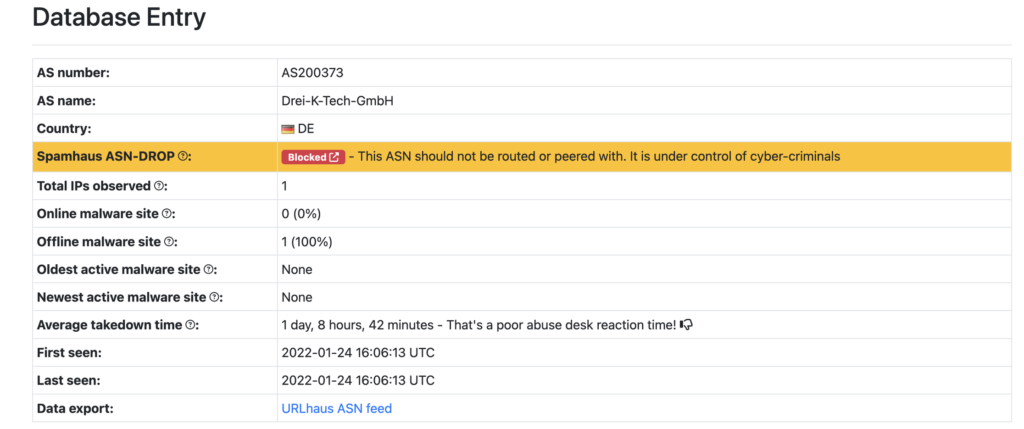
Responding to detected Bad Reputation ASN
I have been building a table that consolidates various ASNs along with their associated information which will grow during the comming weeks after extensive review. This table can be used to review activities originating from the listed IPs and determine how to respond to these actions. For instance, you can leverage the actions available in Defender XDR detection rules, as outlined below:
- Emails received into Inbox Folder from Suspicious ASN/ISP
let suspicious_ISP = externaldata(CIDRASN:int, ASN_Name:string, Information:string)[@"https://raw.githubusercontent.com/Sergio-Albea-Git/Threat-Hunting-KQL-Queries/refs/heads/main/Security-Lists/suspiciousISP.csv"] with (format="csv", ignoreFirstRecord=True);
let CIDRASN = (externaldata (CIDR:string, CIDRASN:int, CIDRASNName:string)
['https://firewalliplists.gypthecat.com/lists/kusto/kusto-cidr-asn.csv.zip']
with (ignoreFirstRecord=true));
EmailEvents
| where DeliveryLocation has "Inbox/folder"
| evaluate ipv4_lookup(CIDRASN, SenderIPv4, CIDR, return_unmatched=true)
| extend GeoIPData = tostring(geo_info_from_ip_address(SenderIPv4).country)
| where isnotempty(GeoIPData)
| join kind=inner ( suspicious_ISP) on $left.CIDRASN == $right.CIDRASN
| project Timestamp,SenderIPv4,DeliveryLocation,GeoIPData,ThreatTypes,CIDR,CIDRASN, CIDRASNName,SenderFromDomain,Subject,RecipientEmailAddress, ReportIdDetection Rule Action: Response : Emails : Move to mailbox folder (ex. Spam), Delete email
- Success Sign-in attempts from Suspicious ASN/ISP
let suspicious_ISP = externaldata(CIDRASN:int, ASN_Name:string, Information:string)[@"https://raw.githubusercontent.com/Sergio-Albea-Git/Threat-Hunting-KQL-Queries/refs/heads/main/Security-Lists/suspiciousISP.csv"] with (format="csv", ignoreFirstRecord=True);
let CIDRASN = (externaldata (CIDR:string, CIDRASN:int, CIDRASNName:string)
['https://firewalliplists.gypthecat.com/lists/kusto/kusto-cidr-asn.csv.zip']
with (ignoreFirstRecord=true));
IdentityLogonEvents
| where Timestamp > ago(30d)
| evaluate ipv4_lookup(CIDRASN, IPAddress, CIDR, return_unmatched=true)
| summarize Different_IPs=make_set(IPAddress), Total_different_IPs=dcount(IPAddress) ,Total_sign_attempts = count(), Suspicious_Sign_attempt = countif((ActionType has "OldPassword") or (FailureReason has "WrongPassword") or ( FailureReason has "validating credentials due to invalid username or password.") or ( FailureReason has "The account is locked, you've tried to sign in too many times with an incorrect user ID or password.") or (FailureReason has "Authentication failed.") or (FailureReason has "UnknownUser") or ( FailureReason has "The user account is disabled." )),
Success_Sign_attempt = count( ActionType has "LogonSuccess"),
Issues_Sign_attempt = countif((FailureReason has "The session is not valid due to password expiration or recent password change.") or ( FailureReason has "General failure")) by ISP,CIDR,CIDRASN
| extend SuspiciousRatio = Suspicious_Sign_attempt * 1.0 / Total_sign_attempts, ValidRatio = Success_Sign_attempt * 1.0 / Total_sign_attempts, IssuesRatio = Issues_Sign_attempt * 1.0 / Total_sign_attempts
| extend SuspiciousPercentage = SuspiciousRatio * 100, ValidPercentage = ValidRatio * 100, IssuesPercentatge = IssuesRatio * 100
| where SuspiciousPercentage > 90
| join kind=inner ( suspicious_ISP) on $left.CIDRASN == $right.CIDRASN
| order by SuspiciousPercentageDetection Rule Action: Response : User : Force Password Reset
Conclusion
In my opinion, while we put significant effort into verifying IPs, domains, URLs, and file hashes, there’s another key player in cybersecurity protection that should take a more active role: ISPs and ASNs. Consider that there are approximately 38,802 ISPs and over 100,000 ASNs worldwide. By identifying and monitoring the risky ones, we can take a proactive approach, staying a step ahead. This would allow us to focus on monitoring these entities rather than tackling individual IPs or domains one by one.
